Airbase — putting security first.
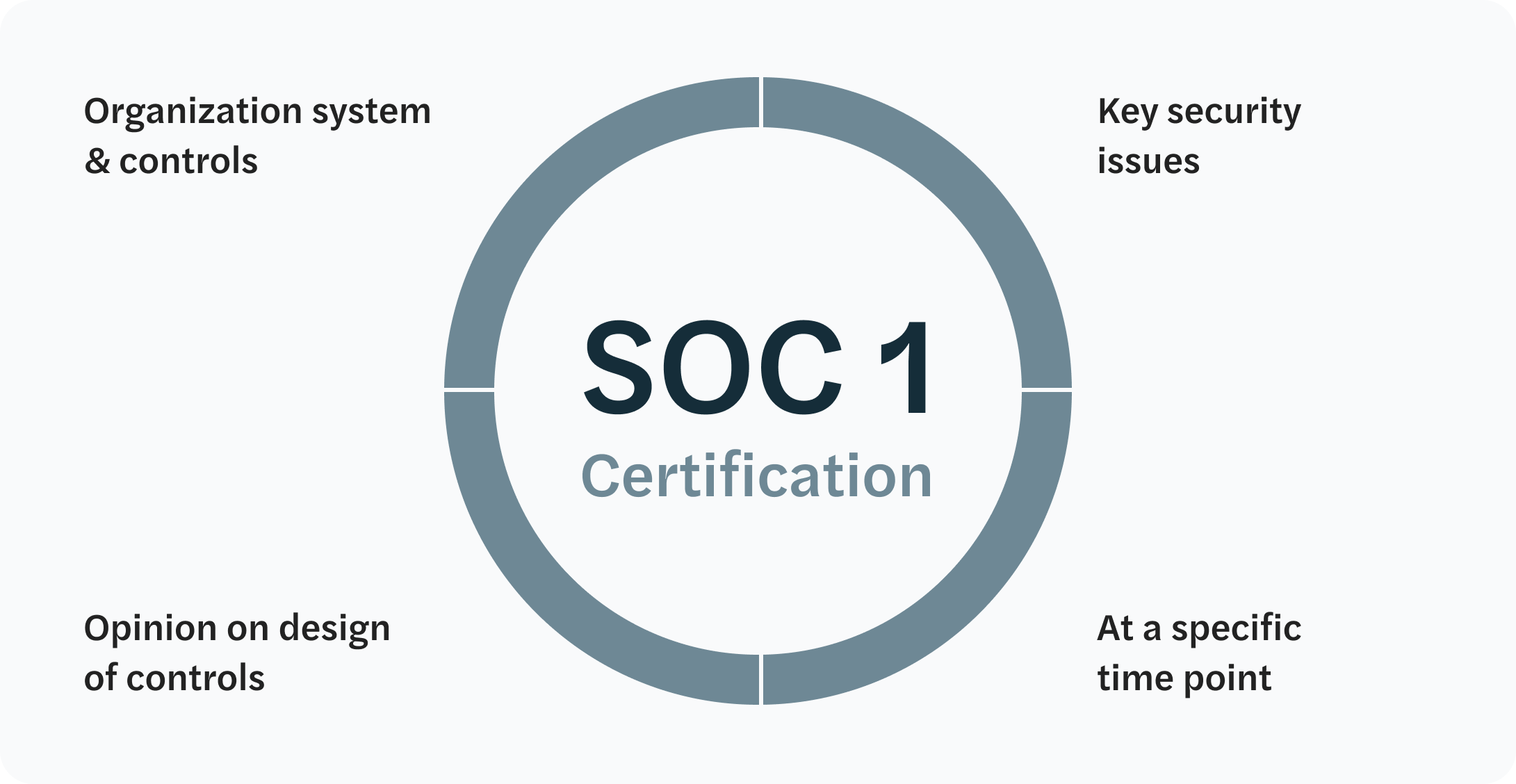
Airbase is a SOC 2 Type II and SOC 1 Type II compliant company and is deeply committed to building and implementing the controls that will help strengthen the security, privacy, and transparency of financial reporting for all of its customers and their vendors. That’s why we use best-practice security procedures for every step in the building and deployment of our software, as well as implementing controls on financial reporting. At the core of our security protocols is SOC, which stands for Service Organization Control. The SOC 1 report represents an audit of our internal controls over financial reporting. The SOC 2 report represents an audit of our controls related to the Trust Criteria of Security, Availability, and Confidentiality.

SOC 1 Type II
SOC 2 Type II
This consistent and rigorous standard provides peace of mind for and clarity to buyers. We’re happy to share our report with you and your compliance team as part of your consideration and buy cycle.
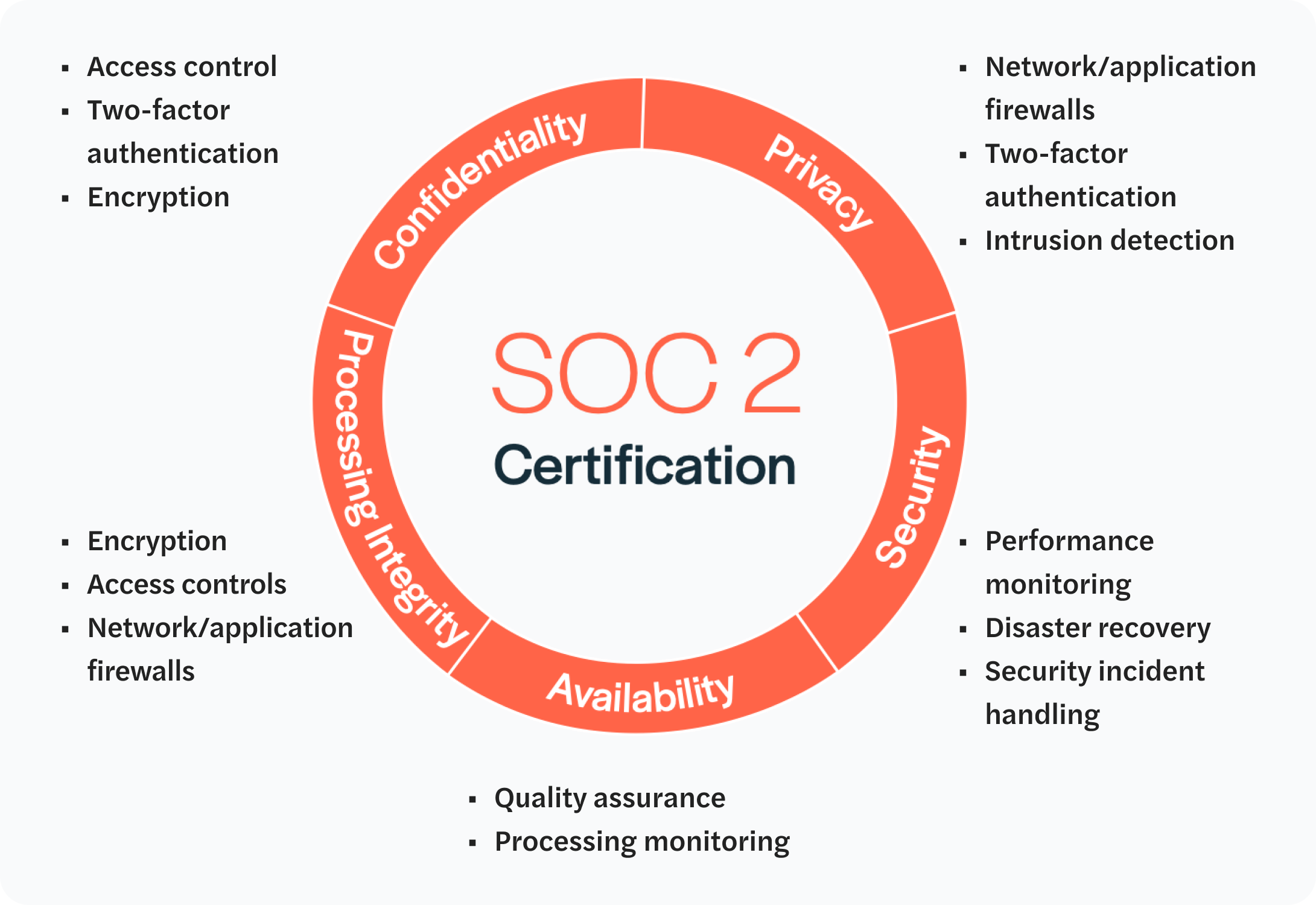
Some of the specific security measures we focus on include:
Secure Access
Access to Airbase is only allowed through a Single Sign-On provider such as Google G-suite, Okta, or OneLogin. Airbase thus does not use or store any passwords on its own. A customer may also choose to enforce additional security policies around SSO access, such as mandating Multi-Factor Authentication (MFA).
Customizable Permissions
Administrators can limit access to several features on a “need-to-know” basis. For example, an administrator can choose to restrict access to sensitive information, such as virtual and physical credit card numbers, or accounting and reporting information, to only personnel who use those features.
Communication
All communication between a user’s device (whether via browser or mobile app) happens through industry-standard encrypted HTTPS connections. Customer data is never sent through the internet over plaintext connections. Furthermore, all communications between Airbase and external service providers take place over encrypted HTTPS connections.
Hosting
The Airbase platform is hosted on the Amazon Web Services platform.
Stored Data
All data stored by Airbase is encrypted at rest with AES-256, block-level storage encryption. In addition, certain sensitive fields in the database are encrypted at the row-level.
Information Security
Airbase never stores any Primary Account Numbers (PAN) for debit or credit cards in systems under its control. All PAN data is stored by Airbase’s partner vendor, who maintains PCI-DSS Level 1 compliance.
Personnel Policies
Airbase requires all its personnel to follow an Information Security Policy that ensures that any devices used for company purposes follow security best practices. Airbase adheres to a defense-in-depth strategy, and only grants its personnel access to resources on a “need-to-know” basis. Airbase also requires its personnel to use a secure vault to communicate any sensitive information internally.
Privacy
We take customer privacy seriously. We make every effort to ensure that the information required is restricted to the minimum amount needed to perform the platform’s normal functions. Airbase personnel’s access to customer information is also restricted to that which is required to assist customers, and Airbase maintains an audit log of all operations that may be performed by its personnel.
 Jira Integration – Streamline Your Workflows
Jira Integration – Streamline Your Workflows  Ironclad Integration – Simplify Legal Operations
Ironclad Integration – Simplify Legal Operations  Asana
Asana